Cybersecured…ish? Is your business prepared for a cyber-attack?
About the author
Kirsty Fletcher-Reid studied the CIPR Professional PR Diploma with PR Academy. This article was submitted as part of an assignment.

The threat that cyber-attacks pose for companies across the maritime industry is huge, but are we doing enough to pre-empt and plan for what many believe is becoming the inevitable?

Reputation management is key to ensuring your business is prepared for what execs don’t like to discuss; the big issues, the melt-downs, the ‘we’ve had a cyber breach and our client data has been stolen’! But what exactly do these risks look like, and is there a foundation to be found based on the technical elements of maritime cybersecurity that can be utilised?
Over 90% of the UK’s visible trade moves by sea. The shipping industry continues to expand to meet the demands of globalisation, and maritime trade has quadrupled over the past 40 years. Throughout industry developments there have been none so fast paced as that of the digital and its ever-developing clutch on day to day maritime operations.
Cyber risks within this industry are therefore not just something that a ‘bot’ or person has left for you or your business online or in your emails to clean up. It’s not a digital take down on your social media, a meme that’s been unanswered or comments to discredit your company, and it’s not paid fake news that one of your competitors have posted. No. In today’s digital landscape we are seeing nearly 17 million cyber-attacks reportedly occurring each week worldwide, and with Marine Traffic showing at least 50,000 ships at sea or in port at any one time, the industry is heightened to the fact that one cyber-attack could bring down multi-million-dollar operations through just one port or vessel takeover, potentially causing our worldwide goods transportation to come a grinding halt.
At its most basic, cyber-attacks come in two formats: untargeted, where a company of a ship’s system and data are one of many potential targets, and targeted; where a company or a ship’s system and data are the intended target. In the past 18 months alone, the industry has experienced several high-profile attacks sending shockwaves throughout.
Despite this glaringly obvious threat, the maritime industry has been slow in educating businesses and future-proofing operations to deal with the challenges on the horizon. This has caused problems not just for business systems and internal people management but has highlighted the key risks that a breach in cybersecurity could trigger for individual businesses, and what appears to be a lack of preparation for reputation management to be in place to combat the issues and risks associated. The increasing reliance on digital communication, automation and the interconnectedness of the global economy has made cyber security within the Maritime industry not only an issue of national security, but one of global security. To the point that 2010 saw the Strategic Defence and Security Review list Cyber Security as a top tier threat to national security, and when the Strategic Defence and Security make something a top tier threat, you know you need to up your game.
What are the risks?
Whatever the risk is, the key is understanding how your company’s reputation is potentially at stake. Getting to grip with the complex risk-issues-crisis management cycle and the internal or external factors that affect it is critical should a cyber-threat/issue come to fruition as a crisis, especially when there are high profile customers with sensitive date involved.
So, what is cyber risk? North P&I (Protection and Indemnity) Association explain cyber risk as ‘any risk of accidents, incidents, financial loss, business disruption or damage to the reputation of an organisation through failure of its electronic systems or by the persons using those systems’. By this definition, any cyber risk is inherently connected to business reputation.
Many of the issues and risks we are experiencing today are heavily tied into the high-tech systems used across operations daily, thus a cyber-attack on these systems is external to the organisation. For example, most vessels have two significant capabilities, each supported by specific hardware and software. All vessels have systems for navigation and propulsion including global positioning systems (GPS), marine Automatic Identification Systems (AIS), and the Electronic Chart Display and Information Systems (ECDIS). The other set of systems are cargo related. Excluding passengers, this is relevant for over 98% of the worlds fleet (as of 2015, United Nations 2015). Most of the 1.7 million ships distributing goods, waste and resources such as oil, are therefore vulnerable via every single one of their automated systems, as well as the clients and ports they interact with.
Based on these systems, Chris South, a senior underwriter for West of England P&I explains that there are four factors at play when it comes to Maritime cyber-threats. The first is automation itself, as machinery on vessels is increasingly controlled by software. The second is integration: on any given vessel, there may be multiple systems interconnected. The third is the ability of ship-to-shore systems that communicate via remote monitoring. The fourth factor is that all these systems are connected through the internet. Virtually any company that now relies on these systems is exposed to a cyber cascade of sorts, where one part of the industry ends up infecting the other.
But how do these vulnerabilities turn into potential issues or risks when it comes to reputation? Recently, Chinese shipping company China Ocean Shipping (COSCO) saw their email and telephone lines taken over, as well as being affected in their communication lines connecting clients through conventional communications and social media. Thankfully no ships were directly affected, and the company was able to successfully isolate the affected network and continue operations normally. However, questions were asked as to how such a huge, international company allowed something as rudimentary as their communications system to be taken over, with many customers voicing their increasing distrust in the company’s internal cybersecurity which in turn had a huge influence on COSCO’s share price.
Another high-profile attack in recent months was the ‘NotPetya’ malware outbreak in October 2017 which struck A.P Moller-Maersk’s IT department, exposing it’s APM terminals and ports worldwide. The closure of ports and the following clean-up of backlog cost Maersk a spine tingling $300 million. On top of that, Maersk had to reinstall its entire infrastructure including 45,000 PC’s, 2,500 applications, and 4,000 servers.
Shipbroker Clarkson’s revealed they discovered a cyber breach in November 2017 which was actually made up to 5 months earlier, with an unauthorised person gaining access to certain company computer systems in the UK pertaining to the loss of commercial and client data which they then held at ransom. Clarkson’s recovered a copy of the stolen data but are now having to go through the process of contacting all those potentially affected in the breach. Not only did this cause huge upset amongst Clarkson’s customers for the sensitive nature of data stolen, but the distrust built up from discovering the breach was made 5 months prior to identification caused for an ugly backlash against the company’s internal securities in place and their own management of the situation.
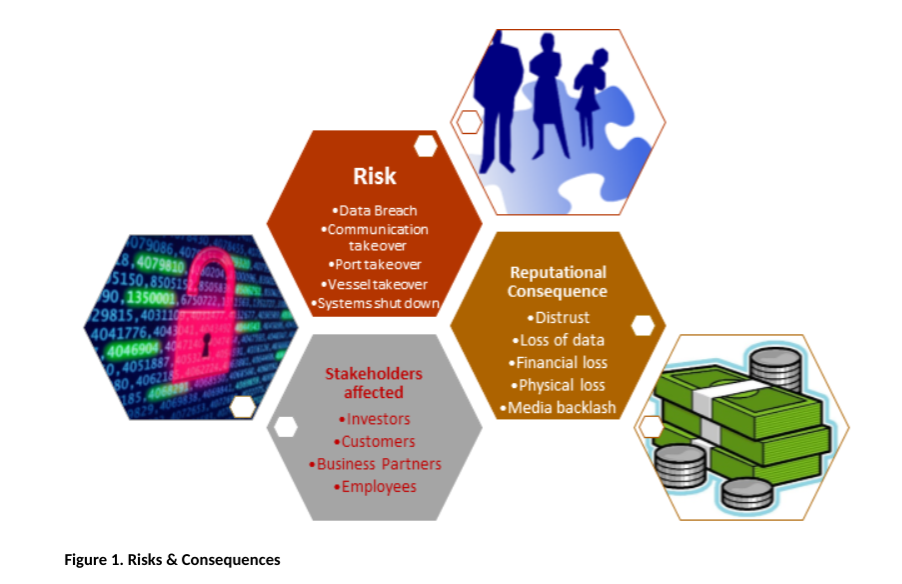
Earlier this year DNV (the Norwegian/German internationally accredited registrar and classification society) class notation released their summary of Cyber Security Threats, highlighting that the annual damage to the global economy from cybercrime is estimated to be between 200-400 billion USD. In addition, according to the CSO Alliance, more than 1,000 individual ships have successfully been hacked in the last five years. Together, statistics and previous attacks allow us to build up a picture of what risks are really going to have an affect on our reputation in the event of an attack. Figure 1 highlights these risks and the issues they can cause.
Where are the industry bodies?
The International Maritime Organisation (IMO) has been late and somewhat slow in considering appropriate assistance and regulation. In 2014, they consulted members on what maritime cyber security should look like. Two years later they issue their interim cybersecurity risk management guidelines which are broad and not particularly maritime specific.
Similarly, the International Ship and Port Facility Security Code (ISPS) and International Safety Management Code (ISM) have provided amendments which demonstrate how port and ship operations should undertake risk management processes. These amendments however, do not come into force until 2021 meaning organisations have little incentive to implement a risk management process right now which in turn means there is little internal assessment or review.
Figure 2 is taken from the Baltic & International Maritime Council (BIMCO) paper The Guidelines on Cyber Security onboard Ships. It has been created as a tool to be used as the industry specific approach to cyber security as a Whole Scheme of Maritime Cyber Security Awareness. This tool is now being used as industry standard.
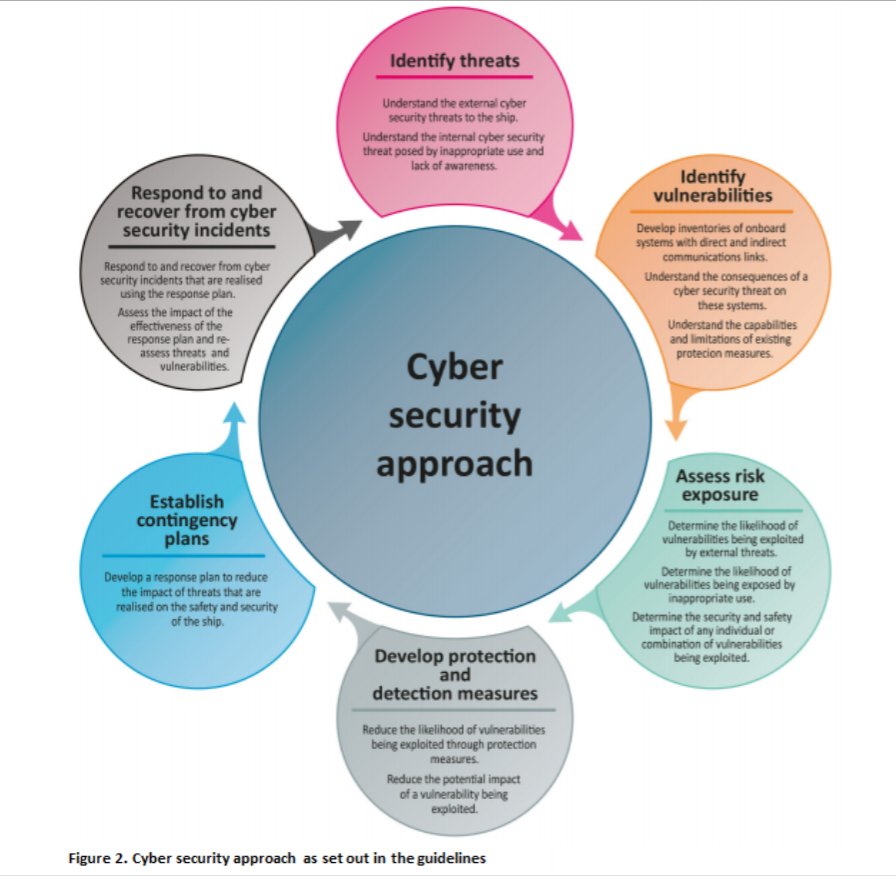
Whilst the underlying theme of this approach is focussed on the technical elements of operational planning, there are key elements which are directly linked to the process of risk management.
If you’re asking yourself how all these management processes are connected, let me explain. Most public relations practitioners commonly distinguish issues management from crisis management with the assumption that an organisation has more space and time to resolve an issue. However, renowned PR practitioner Andrew Griffin explains: ‘What identifies a crisis is not the nature of what has happened but what is at stake – reputation, the bottom line, the licence to operate and the future of the organisation – and the immediacy of the threat.’ He writes that reputation is not to be viewed in isolation, but instead as part of a continuous cycle of risks, issues and emergent crises. In the instance of the all-encompassing cyber security, this cycle works well.
Paul Hopkin, an internationally recognised risk management professional, identifies risk management as providing ‘structured information to assist with business decision making’. It contributes towards effectiveness and efficiency of an organisation’s strategies, processes and both routine and exceptional operations. An integrated approach to risk management should therefore be adopted across an organisation to enable policies to be created that detail processes and procedures, specific responsibilities and compliance within other policy areas.
An integrated approach should therefore enable policies to be created that detail processes and procedures, specific responsibilities and compliance which in turn prepares your reputation management. We must ask ourselves: what can go wrong, how is it likely to happen, and what are the consequences if it does?
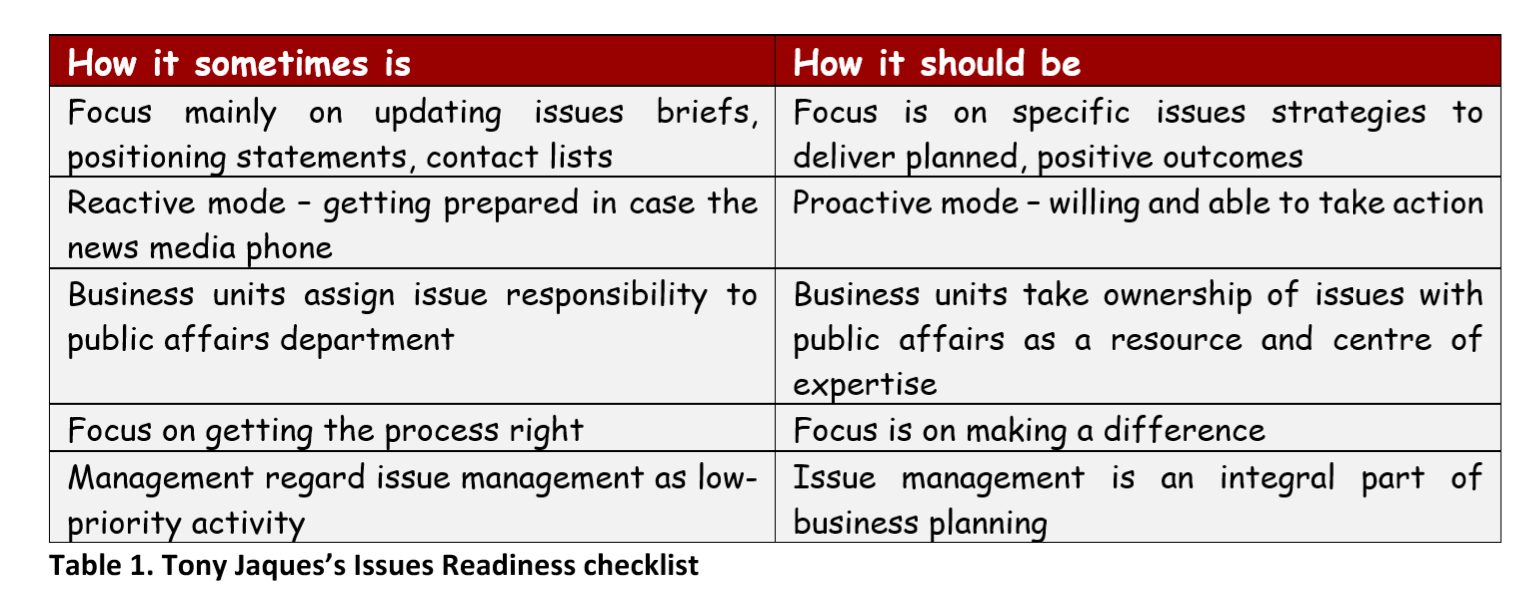
Most organisations do have planning and procedures in place for issues or crisis management, however it can be said that whilst the majority are fit for purpose, they are often not as focused as they could be. Issues & Crisis Management specialist Tony Jaques believes there is a definite ideal vs reality when it comes to what most organisations do when it comes to their own reputation management.
 The way forward
The way forward
Taking into account the idea that most organisations have a foundation of issues & crisis management, there is an opportunity to build on these foundations to ensure a cohesive and well-structured reputation management plan is also in place. We have already touched on the Cyber Security Approach presented throughout the industry from BIMCO, and whilst its technically based, the same pinnacles can be used to create a checklist for your own business based on Andrew Griffins crisis life cycle which attributes good management to being able to Predict, Prevent, Prepare, Resolve, Respond & Recover.
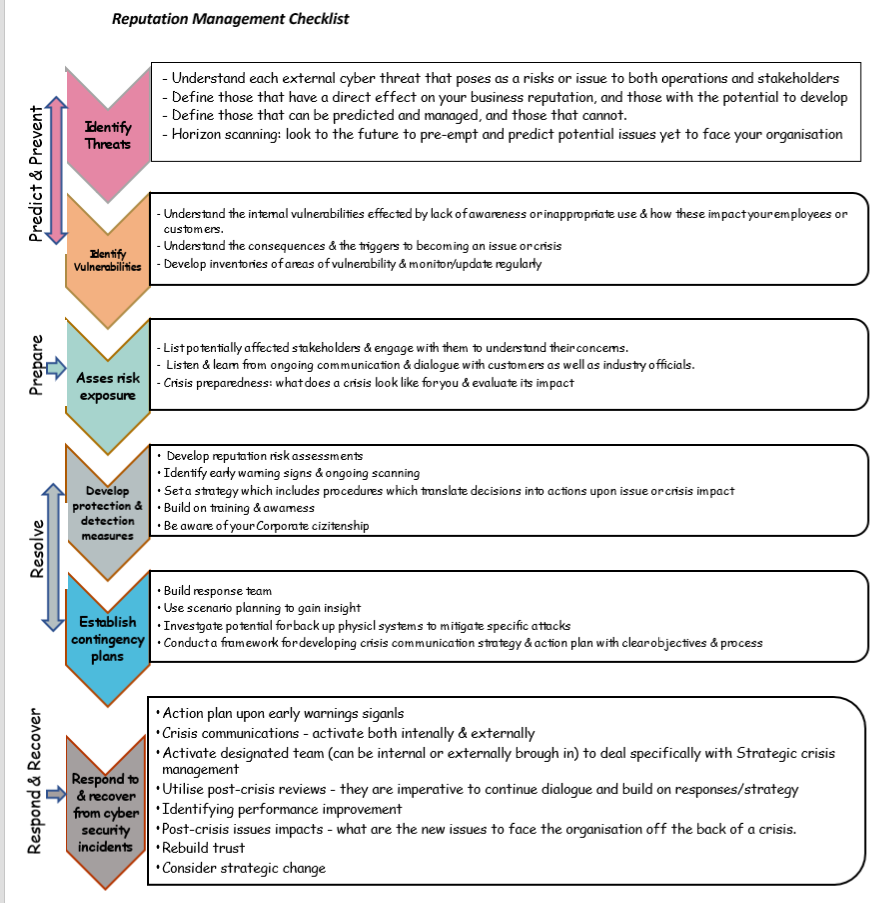
Are you monitoring your reputation?
Building on effective risk and reputation management requires ongoing monitoring of both the technical elements causing cyber issues, and the publics affected. Effective reputation management therefore must include continuous dialogue and communication.
Monitoring your reputation is a tool you can use to gauge how you’re compared in the market. As a result, using the feedback (even if its negative) can help improve your service and remain engaged with your audience. This too can be said for shareholders and employees. A healthy engagement and communication during normal business can really help when there is an issue or crisis to manage, as the building blocks of your relationship are already there for you to utilise should you need to.
It is important to note that, as we’ve already seen, that not all threats can be evaded. Being proactive will ensure that a cyber-attack or other threats will not cause irreversible reputation damage. This means determining the possible threats and building protocols to handle them. Even the best reputation management will still experience repercussions. At the very least, we must be prepared, and continue to measure & monitor in order to develop a quick and appropriate response.
Ultimately, your reputation management will help your business be prepared and resilient, cyber threat or otherwise.
References
- Lyne, James (2013) Ted Talks Everyday Cybercrime – and what you can do about it: https://www.ted.com/talks/james_lyne_everyday_cybercrime_and_what_you_can_do_about_it
- Rider, David (2018) Cyber Security at Sea: The Real Threats: Maritime Executive https://www.maritime-executive.com/blog/cyber-security-at-sea-the-real-threats
- Hopcraft, R. and Martin, Keith (2018) 50,000 Ships Worldwide are vulnerable to cyberattacks: The Independent https://www.independent.co.uk/life-style/gadgets-and-tech/ships-cyberattacks-vulnerable-worldwide-a8404191.htm
- Marine Traffic AIS https://www.marinetraffic.com/en/ais/home/centerx:1.0/centery:61.6/zoom:2
- MARSH Global Marine Practice (2014). The Risk of Cyber-attack to the maritime sector. https://www.marsh.com/content/dam/marsh/Documents/PDF/UK-en/The%20Risk%20of%20Cyber-Attack%20to%20the%20Maritime%20Sector-07-2014.pdf
- Keefe, P (2018) Ports Pushed up to Cyber Security. Maritime Reporter and Engineering News (online version available marine.com)
- The Guidelines on Cyber Security onboard Ships. Published and supported by BIMCO, CLIA, ICS, INTERCARGO, INTERTANKO, OCIMF and IUMI http://www.ics-shipping.org/docs/default-source/resources/safety-security-and-operations/guidelines-on-cyber-security-onboard-ships.pdf?sfvrsn=16
- BIMCO (online presentation) Cyber Security: Can you afford not to do it? http://gia.org.sg/pdfs/Industry/Marine/MKSS/SS36_Presentation_Maite.pdf
- Verizon (2018) 2018 Data Breach Investigations Report. What went wrong? Online Report https://www.verizonenterprise.com/verizon-insights-lab/dbir/
- Transport Minister Lord Callanan (2017) Speech. Protecting the maritime industry from cyber attacks. https://www.gov.uk/government/speeches/protecting-the-maritime-industry-from-cyber-attacks
- How, E. Thurlbeck, M. and Garcia-Perez, A. Towards cyber security readiness in the Maritime Industry: A knowledge-based approach. https://pdfs.semanticscholar.org/0bca/56d7f4c56899540d3ee9180ee6c8557a813b.pdf
- Professor. Forbes, V. L (2018) Associate Paper: The Global Maritime Industry remains unprepared for future cybersecurity challenges. Future Directions International. http://www.futuredirections.org.au/wp-content/uploads/2018/08/Global-Maritime-Industry-Remains-Unprepared-for-Future-Cybersecurity-Challenges.pdf
- Inmarsat Publication (2018) Inmarsat takes a mature approach to maritime cyber security.
https://docs.wixstatic.com/ugd/9491c8_49ad5c4cd9924bfc9126461d28e14c84.pdf - The North of England P&I Association (2016) Loss Prevention Briefing for Members. Cyber Risks in Shipping. https://docs.wixstatic.com/ugd/9491c8_11515b8407fc49cea99e5a623ae7c880.pdf
- Fritton, O. Prince, D. Germond, B and Lacy, M. (2015) The Future of Maritime Cyber Security. Lancaster University EPrints https://docs.wixstatic.com/ugd/9491c8_44c7f1a31c514f8db3bfbba20f0b2e64.pdf
- Bailey, S (2017) PR Week Are your communications teams clued up on cybersecurity? https://www.prweek.com/article/1441766/communications-teams-clued-cybersecurity
- Field, J (2018) IPR Institute for Public Relations Creating a culture of cybersecurity awareness. https://instituteforpr.org/creating-a-culture-of-cyber-security-awareness/
- Jenson, L. (2015) Article in Technology Innovation Management Review, Carleton University. Challenges in Maritime Cyber-Resilience. https://timreview.ca/sites/default/files/Issue_PDF/TIMReview_April2015.pdf#page=35
- Dr. Bada, M. & Professor Sasse, A. (2014) Global Cyber Security Capacity Centre: Cyber Security Awarenss Campaigs, Why do they fail to change behaviour? http://discovery.ucl.ac.uk/1468954/1/Awareness%20CampaignsDraftWorkingPaper.pdf
- Viveros, M (2013) Harvard Business Review Cyber Security Depends on Education. https://hbr.org/2013/06/cyber-security-depends-on-educ
- Hellenic Shipping News Worldwide (2018) Cybersecurity in the Maritime Industry https://www.hellenicshippingnews.com/cybersecurity-in-the-maritime-industry/
- Jones, KD. Tam, K & Papadaki, M. (2015) Threats and Impacts in Maritime Cyber Security. University of Plymouth file:///C:/Users/kirsty.fletcher-reid/Downloads/Jones_Tam_Papadaki_2016_Threats_and_Impacts_in_Maritime_Cyber_Security_Final.pdf
- Agnes, M & Jaques, T (2015) The Crisis Intelligence Podcast. #027 – Successful Issue Management with Tony Jaques https://www.youtube.com/watch?v=oBxbiV5BDf8
- The Economist (2018) How Europe can improve the development of AI. https://www.economist.com/leaders/2018/09/22/how-europe-can-improve-the-development-of-ai
- Griffin, A. (2014) Crisis, Issues and Reputation Management: A Handbook for PR and Communications Professionals. Kogan Page.
- Jaques, T. (2014) Issue & Crisis Management: Exploring issues, crises, risks & reputation. Oxford University Press Australia
- Bailey, R. (2018) Public relations as reputation management. https://www.prplace.com/blog/posts/2018/february/public-relations-as-reputation-management/
- DNV.G: Cyber security threats in maritime industry. (Jan 2019) https://www.bluemaritimecluster.no/download?objectPath=/upload_images/18D93FF3B5F54B63BE217F98A6DF7CB2.pdf
- YouTube. Jones, K. Cyber-attacks pose great threats in maritime industry. (2018) Plymouth University. https://safety4sea.com/watch-cyber-attacks-pose-great-threats-in-maritime-industry/